Surveillance Security
Understanding cyber surveillance, digital track of your data and the power of control of those who collect them


What is Cyber Surveillance?
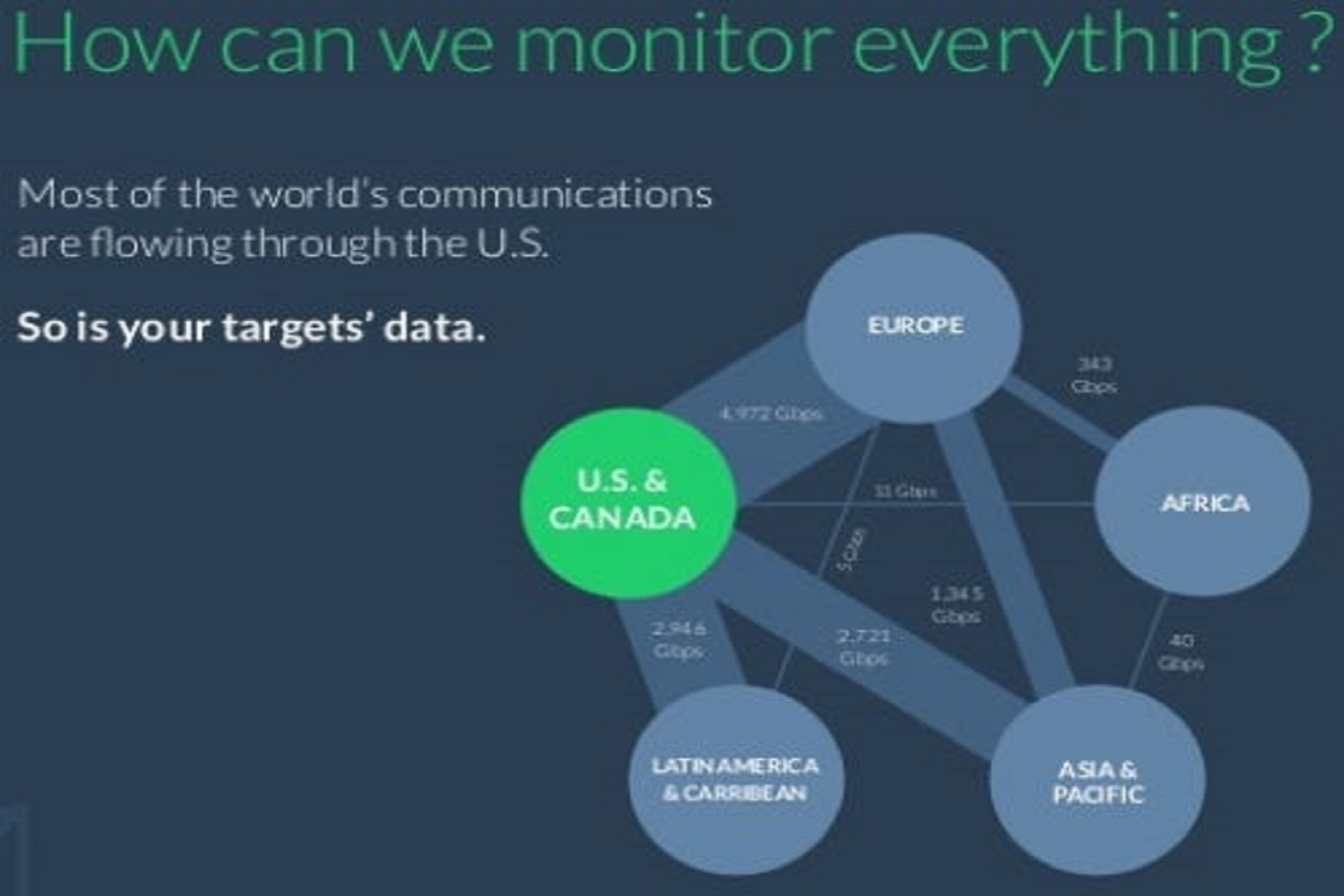
Cyber surveillance is the monitoring of computer activity and data stored locally on a computer or data being transferred over computer networks such as the Internet. This monitoring is often carried out covertly and may be completed by governments, corporations, criminal organizations, or individuals. It may or may not be legal and may or may not require authorization from a court or other independent government agencies. Computer and network surveillance programs are widespread today and almost all Internet traffic can be monitored.
Surveillance allows governments and other agencies to maintain social control, recognize and monitor threats or any suspicious activity, and prevent and investigate criminal activities. With the advent of programs such as the Total Information Awareness program, technologies such as high-speed surveillance computers and biometrics software, and laws such as the Communications Assistance For Law Enforcement Act, governments now possess an unprecedented ability to monitor the activities of citizens.
There are different forms of digital surveillance:
Social network analysis – One common form of surveillance is to create maps of social networks based on data from social networking sites as well as from traffic analysis information from phone call records such as those in the NSA call database, and internet traffic data gathered under CALEA. These social network “maps” are then data mined to extract useful information such as personal interests, friendships and affiliations, wants, beliefs, thoughts, and activities
Malicious software – In addition to monitoring information sent over a computer network, there is also a way to examine data stored on a computer’s hard drive, and to monitor the activities of a person using the computer. A surveillance program installed on a computer can search the contents of the hard drive for suspicious data, can monitor computer use, collect passwords, and/or report back activities in real-time to its operator through the Internet connection
Corporate surveillance / Surveillance capitalism – Corporate surveillance of computer activity is very common. The data collected is most often used for marketing purposes or sold to other corporations, but is also regularly shared with government agencies. It can be used as a form of business intelligence, which enables the corporation to better tailor their products and/or services to be desirable by their customers. The data can also be sold to other corporations so that they can use it for the aforementioned purpose, or it can be used for direct marketing purposes, such as targeted advertisements, where ads are targeted to the user of the search engine by analyzing their search history and emails (if they use free webmail services), which are kept in a database. (Click here to learn more about Corporate surveillance and Surveillance capitalism).
Network surveillance – The vast majority of computer surveillance involves the monitoring of personal data and traffic on the Internet. For example, in the United States, the Communications Assistance For Law Enforcement Act mandates that all phone calls and broadband internet traffic (emails, web traffic, instant messaging, etc.) be available for unimpeded, real-time monitoring by Federal law enforcement agencies
Overview Services
We offer methods of protection against surveillance through the use of technical tools (change of operating system, VPN, use of software focused on protection, and others) and through individual consultations, we teach and offer guidance on behavioral tactics that help the user to remain anonymous and use the digital services in a private way.
Additional protection methods are offered, such as camera removal and microphone removal from devices, signal blocking in stand-off mode and other tactics to protect the user.
Contact us for more information.

Security Services
Our security services use the most advanced methods of protection available and we use the best tools on the market

Privacy Services
Our privacy and anonymity services are effective and are set up uniquely for each user. In addition to individual support tailored to the needs of our customers

Industry Certified
Companies are already adapting to the rapidly changing digital world and are using our services to protect themselves
Testimonial
Clients Feedback
See what some of our customers think about our services
Thank you for teaching me how to protect myself when using my smartphone, avoid falling victim to scams, losing money through online transactions, and identifying spam. As someone who has fallen for online scams before, I now feel much more informed and secure.
Import company
Quality protection methods offered to implement in our company, we are satisfied with the service provided
User
Really after we discover the threats of the digital world I am much more calm in knowing that I am safe and protecting my data
Privacy, anonymity and security are essential for using digital services today. Thanks 99% Security for helping me achieve this
Tech Company
Essential services for any company—simple techniques and easy actions that may seem unnecessary but make all the difference. We loved the service; it completely changed our team’s mindset.



Maria R.
User